I could still see the situation quickly turn into a Lebanon type of situation but for the first time Iraqi security forces really stood toe-to-toe with Mahdi and held their own.
Monday, March 31, 2008
Iraq Begins to Stand on its Own Two Feet
Sunday, March 30, 2008
Historians Weigh in On Iraq
a consensus amongst these academics would imply that most historians feel that the U.S. will be in Iraq for quite some time.
Is Iraq the New Lebanon?
Iraq with Sadr loose could be another Lebanon and if Maliki calls off the dogs now that Sadr has asked for relief, this would be a mistake. The government should keep the pressure up and press the attack until weapons are turned in, although Sadr has stated that he does not to give up his weapons.
Rogue Scanner
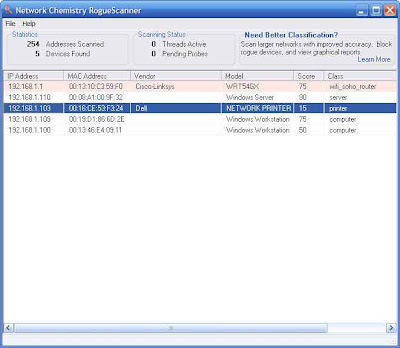
I've reviewed network tools with some suggestions but Rogue Scanner may be a better way to find out whether your network has any intruders on it. Before running this program you can assemble a list of every PC and device on your network. Thereafter by deploying RogueScanner you will have a list of every device on your network, including routers, printers, PCs and items. The IP and MAC addresses are listed but even more it investiages even further to find additional information such as whether the device is a workstation, printer, server, router or PC, as well as the manufacturer and model number.
You can then compare notes between your list and what the program finds with the list of devices that you know are safe and secure. If there is something that does not look famaliar then your system has been compromised.
Saturday, March 29, 2008
Basra: At the Worst, Same as It Ever Was

Today's violence is more of the same and there is no clear-cut result to the day's activity at the very least. On the other hand, despite the typical mainstream Western press which misses the boat nearly all the time, the Mahdi militia is experiencing heavy losses. The Western press appears to report stories based on what it would like presented, rather than reporting what actually is occurring. Thus, Mahdi is really being tested severely, rather than Basra being a test of the admittedly fragile Iraqi government. To wit, since fighting started Tuesday 347 Mahdi Army fighters were killed, 531 were wounded, 343 were captured, and 30 surrendered. Coalition forces killed 125 Mahdi Army fighters in Baghdad alone, while Iraqi security forces have killed 140 Mahdi fighters in Basra. While estimates of the Mahdi Army is debatable, most analysts postulate the Mahdi between 40,000 to 60,000. Since an estimated 1,000 Mahdi fighters were killed, captured, wounded and surrendered, the Mahdi has an attrition rate of 1.5 to 2.5 percent over the past five days. That attrition is a significant attrition.
Friday, March 28, 2008
Apple Easiest to Cherry Pick

For only two minutes work Charlie Miller, an analyst at Independent Security Evaluators (ISE), a Baltimore-based security consultancy, walked away with $10,000 by hacking into a MacBook Air. The easiest exploit of the three options was the Mac OS X. The MacBook Air was running the current version of Mac OS X, 10.5.2, with all the latest security patches applied. The other two computers included a Sony Vaio VGN-TZ37CN running Ubuntu 7.10 and a Fujitsu U810 notebook running Windows Vista Ultimate SP1, were also up to date and fully patched.
Basra Analysis
With these three elements in mind, and in any case, the Basra case will be revealing.
Thursday, March 27, 2008
AbiWord: Free and Lite and Easy

One of the most frustrating aspects of computing really should be one of the simplest. Where can a guy find simple, free word processing software? Either word processors are too expensive or software is incompatible with other versions. Enter AbiWord which may change all that.
I use NoteTabLite for most of my wordsmithing but word processors are more difficult since they don't always play nicely with each other. AbiWord seems to do the trick for most common uses.
For the most straightforward word processing tasks such as manipulating images AbiWord is the freebie to use. The GUI is simple and uncomplicated. It does have enough features to do more complicated tasks, without making word processing terribly complicated. I generally need a few things such as adding page numbers, date and time, and this tool includes these additional features.
The free program requires a Windows 2000 or Windows XP OS.
Wednesday, March 26, 2008
Sarkozy Does Not Make a Crowd
Among the issues that Sarkozy wished to address are energy, immigration, as well as security and defense.
Sarkozy hopes that the EU can be strengthened with the participation of the British.
I already noted here that Sarkozy has made an Afghanistan pledge. He plans to add additional French troops to the effort.
Sarkozy stated: "We cannot afford to lose Afghanistan. We cannot afford to see the Taleban and Al Qaeda returning to Kabul. Whatever the cost, however difficult the victory, we cannot afford it. We must win."
Until Sarkozy, France and the U.S. have often been at odds, and Sarkozy added in her comments: "I perfectly understand that Britain should wish to keep its special relationship with the US, but that doesn't stop Britain from taking its rightful place in Europe."
I don't think three is a crowd. At this point, I see no reason why Britain and France can not contribute more to the Coalition.
Tuesday, March 25, 2008
Obama's Taxes
On their 2006 tax return, Obama and his wife, Michelle, earned over $991,000 in 2006 and paid $277,431 on the income.
More than half of the couple's income is a direct royalty from Obama's books--nearly $507,000: The Audacity of Hope and Dreams From My Father. In 2005, Obama earned over $1,210,000 from royalties.
The Obamas earned nearly $431,000 in wages in 2006. The Senator's salary was $165,000.
The couple also earned more than $51,000 from Treehouse Foods, an Illinois-based food manufacturer where Michelle Obama served on the Treehouse board.
Before 2005, the couple had more modest incomes. Between 2000 and 2004, they earned between $207,647 and $275,123 a year.
Monday, March 24, 2008
Non-U.S. Citizens Serve in the Military
The answer to that question is the estimated 20,500 "non-U.S. citizens"--serving in all branches of the U.S. military.
Indeed, the first U.S. service member killed in the Iraq war, on March 21, 2003, was Marine Lance Cpl. Jose Gutierrez, a native of Guatemala.
Active-duty non-citizens who have served honorably in war on or after September 11, 2001, may "file for immediate citizenship," according to the Defense Department.
Nearly 37,000 non-citizens of the U.S. armed forces have been granted citizenship since the war on terror began in October 2001; 109 have been granted posthumously, according to the U.S. Citizenship and Immigration Services.
Another 7,300 still have their requests for citizenship pending.
Historically, we have had immigrants in the military dating back to the Revolutionary War.
Sunday, March 23, 2008
Tepid Network Solutions Bows to Islamic Pressure

American hosting services can accommodate military service personnel being shot but goodness gracious they can not show a Dutch politician who was planning to release a film critical of Islam.
The tepid hosting service, Network Solutions, said it was investigating complaints on hate language. The Terms of Service excludes "material that is obscene, defamatory, libellous, unlawful, harassing, abusive... hate propaganda" and "profane, indecent or otherwise objectionable material of any kind or nature."
Dutch politician Geert Wilders says the 15-minute film describes Islam as "the enemy of freedom." If this is hate language, then we are all in trouble.
The film has effectively been silenced by protests in many Muslim countries and condemned by Iran and Pakistan.
Wilders' film is entitled Fitna, Arabic for strife or discord, usually religious.
Wilders stated that "Islamic ideology has as its utmost goal the destruction of what is most dear to us, our freedom," and in this he is correct as he stated in a commentary for the Dutch publication De Volkskrant.
Not only is Wilders on what in America should be sound 1st Amendment ground but he is proving prophetic as well.
Saudi Government Trains for Prayer
Saturday, March 22, 2008
Bombing Distinction for Germany
 Graphic source: Times Online, Roger Boyes
Graphic source: Times Online, Roger Boyes
As most of Europe has been slow to support the Coalition the war on terror increasingly comes home to roost. To wit: a clerical worker was named as Germany's first suicide bomber in Afghanistan.
Cueneyt Ciftci, 28, who was born in Freising, Bavaria to a family of Turkish immigrants, is believed to have driven a pick-up truck filled with explosives into a U.S. guard post.
German police trace him to a network that appears linked to radical Bavarian mosques and to a group arrested last September for preparing explosives to bomb Frankfurt airport.
The bomber married and had two children but more recently resigned his clerical position. His resignation seems to have been organized by Adem Yilmaz who is under arrest after police raids broke up his cell preparing for an attack on Frankfurt airport, Ramstein airbase, and other U.S. targets in Germany. The other cell members, Fritz Gelowicz and Daniel Schneider, were native Germans.
There appears to be connections between radical clergy, a mosque in Ulm in particular seems to have inspired many and the movement of preachers between Pakistan and Europe and the access to training camps close to the Afghan border have made some German Muslims regular pilgrims.
As Sarkosy has committed more troops to Afghistan, perhaps Merkel can plot a similar course. Europe should be committing more effort to security in the Middle East.
U.S. Top Spot for Iraqis

We hear in the news every day that the Iraqis are displeased with the U.S., nonetheless, the U.S. remains the top destination for refugees.
Friday, March 21, 2008
"The Real Living Culture Is Western Culture"
commentators, such as Muhammad Al-Mahmoud, who make sense.
Obama Consistently Wrong On Iraq
and has differed from Senator Clinton on only one, of eighty-five votes.
Lessig to Change Congress
Lessig's new Web project is Change Congress which aims to convince members of Congress to commit to one or all of four broad pledges: to not accept PAC or lobbyist contributions, to abolish earmarks, to support public financing of public elections, and to drive transparency in the work of Congress.
Thereafter, politicians will be supplied with code to embed word of their pledges on their own Web sites. In addition, the politician's actions related to his or her pledges will be tracked with a Google mashup map and through a wiki.
Most Internet initiatives towards political reform are high-minded but most have accomplished little. The idea here is to build upon the best of Internet social and community activism with the end of substantial reform. With Congress' popularity rating in the low 20s, anything is worth a chance.
Sarkozy to Send 1,000+ Troops to Afghanistan
The troops are a clear expression that Sarkozy is underlining his commitment to the alliance France already has 1,900 soldiers in Afghanistan. Sarkozy stated shortly before Christmas: “There is a war going on here, a war against terrorism, against fanaticism, that we cannot and will not lose.”
Canada has 2,500 troops operating in Kandahar province in the south but had stated that it would pull out next year unless another NATO country offered to send at least 1,000 soldiers to back them up.
Thursday, March 20, 2008
Obama's Passport Breached Repeatedly
The violators are private contract employees working for the U.S. Department of State and they have repeatedly accessed U.S. Senator Barack Obama's passport records over the past three months. Two of the workers have been fired by their employers.
However, the actions of the three separate workers, employees of two different contractors, were described by State Department spokesman Sean McCormack as "imprudent curiosity." More will unfold as the research into the breach continues.
Beckstrom the Starfish

Technology entrepreneur and co-author of The Starfish and the Spider: The Unstoppable Power of Leaderless Organizations,
Rod Beckstrom will be named to run the new National Cyber Security Center at the U.S. Department of Homeland Security. Beckstrom was also founder of Cats Software and co-founder of Twiki.net, a company that offers an open-source wiki software system.
This may be a good appointment since Leaderless illustrates a sound point or two about adaptable cyber era organizations. If a spider's head or a leg is cut off it cannot function. However, if a starfish loses an arm—or two or three—it regenerates them, and all without brain ordering the organism.
Likewise, organizations traditionally followed a spider form. Nonetheless, nimble organizations, whether they be illicit, such as as-Qaeda, or capitalist, such as current entrepreneurial open-source companies, fall into the starfish category.
With the criteria of fighting fire with fire, Beckstrom understands the challenge of transforming traditional bound government organizations to the adaptable and nimble units of modern warfare.
Beckstrom points out that decentralization continue to change industry and society and it is a force to be reckoned with.
Wednesday, March 19, 2008
Audio Message Crusades Against the West
 Graphic source: a propaganda site for Islamofascists, al-Sahab, the media wing of al-Qaeda.
Graphic source: a propaganda site for Islamofascists, al-Sahab, the media wing of al-Qaeda.
In a voice that has not yet been confirmed to be Osama bin Laden,
the speaker whines about the fact that the EU, specifically the best-selling Danish newspaper Jyllands-Posten, is re-printing the cartoons that satirized Muslims who are bombing innocents.
In the continued attack upon Western institutions and other religions, the voice crusades against Pope Benedict XVI.
It may be hard to believe that Islam is the alleged `religion of peace' given the fact that the audio is accompanied with a graphic characterized by a still image of bin Laden holding an AK-47.
Sorry to hear that Islamofascists are having a bad hair day.
Tuesday, March 18, 2008
Audacity of Obama
Obama represents a profound loss for this country. He consciously distances himself from civil rights. The country is clearly ready for an African-American President, but he is not representative of an individual who can move that dream forward. Timing is everything and this is not Obama's time. He is too far removed. Note how he parts company with Rev. Wright, and the civil rights movement. Obama states:
What's remarkable is not how many failed in the face of discrimination, but rather how many men and women overcame the odds; how many were able to make a way out of no way for those like me who would come after them (in the Civil Rights struggle).
Obama has only benefited from civil rights, he did not work for them.
Also, I find it interesting that YouTube plays such a significant role in the controversy but Obama knew Wright, not from a clip, as he was an intimate friend and client. He should have known better and a note to Obama, if a pastor of a church preaches "God damn America"
in a sermon, its time to leave and take your children out of there.
If that point is not enough, Obama and Wright's church, the United Church of Christ General Synod XV also passed a resolution:
concerning the conflict between Israel and Palestinians in the Middle East. . . . named `Tear Down the Wall', [which] calls upon Israel to remove the separation barrier between Israel and the West Bank. Opponents of the `Tear Down the Wall' resolution have noted that the wall's purpose is to prevent terrorist attacks, and that the resolution does not call for a stop to these attacks. The Simon Wiesenthal Center stated that the July 2005 UCC resolutions on divestment from Israel were `functionally anti-Semitic'. The Anti-Defamation League stated that those same resolutions are `disappointing and disturbing' and `deeply troubling'. In addition to the concerns raised about the merits of the `economic leverage resolution, additional concerns were raised about the process in which the General Synod approved the resolution. Michael Downs of the United Church of Christ Pension Boards (who would be charged with implementing any divestment of the UCC's Pension Board investments) wrote a letter to UCC President John Thomas expressing concern `with the precedent-setting implications of voted actions, integrity of process and trust.'
Another note to Obama, if a church votes and in a public manner illustrates anti-Semitic tendencies, you should leave, and take your children out of there.
Monday, March 17, 2008
The First Internet War
 Graphic source: The masked and fearful
Graphic source: The masked and fearful
The new media is heavily invested in the Iraqi situation. The range of blogs runs the gamut from the approved Multi-National Force Iraq website of Operation Iraqi Freedom as well as the registered and published according to Pentagon guidelines type of blog by 1st Lt. Matt Gallagher. On the other hand, an outlaw soldier's blog exists at The Unlikely Soldier. The wide range of soldier blogs can be found at a list of soldier blogs.
But, that is not all, the enemy is active and maintains a propaganda site at the Islamic Army in Iraq blog.
But finally, not to be outdone, in order to stop offensive and objectionable content from airing on American websites the cyberwarfare slogs on at Stop the Internet Terrorists blog site.
How One Person Can Shut Down a Terrorist
These concerned persons can do something about offensive videos. One such site, Stop Internet Terrorists provides a `How to.' The site states:
Our mission - remove as many of these videos as possible! Then maybe YouTube will take it upon themselves to join us in trying to preserve what our military fights for every day: Life! Liberty! The Pursuit of Happiness!
The site also provides directions:
How to Flag (tag) a Video and Shut it DOWN!
Just follow these six easy steps!
1. Click on the first numbered video listed to the right (a full list is available on the Stop Internet Terrorists site.
2. If you see "Confirm Birth Date," click on it. This is your agreement that you are 18 or over.
3. When the video appears, STOP or PAUSE it a few seconds after it has launched if you don't want to watch. If you choose to watch, we can tell you that you need a strong stomach. These videos are offensive, graphic, and very upsetting to some.
4. Just below the video, click on "Flag". This will then open another view that gives you the option to "Select a Reason" as to why you are flagging this video.
5. Then click "Flag This Video" button to the right.
6. There will be an area now right under "Flag" that will then be highlighted saying "Thank you for sharing your concerns".
Congratulations! You have just flagged your first Internet Terrorist Video!
That's it!! Now, just click the back arrow to our site and notice the video you just flagged has changed color! It's a simple tool for visually seeing what you have or haven't done.
And please, if you would, go to the second video and repeat the same process as above until all videos are done!
That's really quite simple and anyone can do it. The world does not need any more violent images than it already has and the terrorists are denied one more outlet for illegitimately spreading their message. Any time the terrorists would like to debate in an open and public forum would be fine. However, I see no reason why they should be able to take advantage of American technology and laxity in regards to denying offensive, hateful speech.
Guarded Optimism About Vital Indicators
 Graphic source: The New York Times
Graphic source: The New York Times
Amidst a recent survey in which at least half of Iraqis have reason for guarded optimism about the future, the Times published a list of vital indicators. While not rosy, there are reasons to think that Iraq may have a chance to be a coherent nation again. The cost is high, the road is fraught with obstacles, but for the first time in five years, there is reason to think that events may unfold in a more positive manner.
Sunday, March 16, 2008
Iraqis: Blood for Oil
In February, American troops detained Ghalib Ali Hamid, the intelligence and internal affairs chief of the Oil Protection Force at the refinery, on suspicion of skimming fuel profits and having ties to insurgents. Graphic source: The N.Y. Times
The N.Y. Times reports that the Baiji refinery "may be the most important industrial site in the Sunni Arab-dominated regions of Iraq." On a peak production day 500 tanker trucks leave the refinery filled with fuel with a street value of $10 million.
Unfortunately, many Iraqis divert at least one-third, and possibly much more, of the fuel from Iraq’s Baiji refinery to the black market. Tankers are hijacked, drivers are bribed, papers are forged and meters are manipulated. And to top it off, at least some of the money reaches insurgents who are still killing more than 100 Iraqis a week.
The American military claims that greed, far more than jihadist ideology, is the critical motivator for a majority of Sunni insurgents.
To combat the financial motivation, at least 91,000 Iraqis, many of them former enemies of the American forces, receive a regular, American-paid salary for serving in neighborhood militias.
In the Salahuddin area of the refinery for example, there were eight pre-war local gas stations, a figure that has ballooned to fifty. The reason is not economic growth but graft.
The Times reports that:
Gas stations are often built just to gain the rights to fuel shipments, at subsidized government rates, that can be resold onto the black market at higher prices. New stations cost more than $100,000 to build, but black market profits from six or seven trucks can often cover that cost, and everything after that is profit, said officials who have studied the scheme.
During last year, the Pentagon estimated that as much as 70 percent of the Baiji refinery’s production, or $2 billion in fuels like gasoline, kerosene and diesel, disappeared annually into the black market.
The insurgents have their agents at all levels, and some are the watchdogs who are supposed to oversee the operation. In February, American troops detained Ghalib Ali Hamid, the intelligence and internal affairs chief of the Oil Protection Force at the refinery, on suspicion of skimming fuel profits and having ties to insurgents.
Although Al Qaeda receives the bulk of Western attention, many in the U.S. military question the numbers and loyalty of average Iraqis for the group. In the opinion of U.S. middle-level troops, jihadist ideology is secondary to the financial incentive of average Iraqis who need to earn a living.
The other major guerrilla groups in the country are Jaish-e-Muhammad, or the Army of Muhammad, which includes ex-Baathists and former military officers, who continue to battle American forces. Some American officers consider the Islamic State of Iraq, to be a front group for Al Qaeda in Mesopotamia.
But other groups such as the 1920s Revolutionary Brigades and Jaish al-Islami, or the Islamic Army, have agreed to support American-financed Sunni militia forces.
The question is whether bribing former insurgents to stop attacking American forces is an effective counter-terrorism force, or whether developing a more secure economic infrastructure would solve the problem. American officers are concerned that the failure to incorporate these Sunni militiamen into the government of Iraq or find them other jobs could portend trouble.
As we might say, you have to do what you need to in order to survive.
Senators Lining Up to the Trough
Clinton received $342 million in earmarks last year, ranking her 10th highest in the Senate, according to the budget watchdog group Taxpayers for Common Sense.
Obama in fiscal year 2008 secured $98 million in funding for Illinois projects, according to the same group. Although Obama voted with McCain, Obama indicates that he requested $311 million in earmarks for the same year.
His total requested funding was about $330 million. His average request was about $2.4 million, with the largest request being $62 million intended to modify a Boeing 747 aircraft to capture infrared images of the Earth.
Saturday, March 15, 2008
Who Makes a Good Bomber?
Saudi Arabia is the single largest point of origin. Al-Qaida is a primary recruiter.
The study profiles 48 foreign fighters who were captured or surrendered. The interrogators of the study concluded that most foreign fighters are Sunni Muslim men from 18 to 30, with the mean age of 22. They are almost always single males with no children, and tend to be students or hold blue-collar jobs ranging from taxi drivers to construction and retail sales. The majority of the bombers have six to 12 years of schooling, with very few having gone to college. Most come from families in the poor or middle-classes and have six to eight siblings.
According to the National Counterterrorism Center in Washington, 949 suicide bombers killed 10,119 people and wounded 22,995 from the beginning of 2004 until now. Data compiled by the AP through its own reporting found that between April 28, 2005 and March 13, 2008 there were 708 incidents involving suicide bombings, with a total of 14,633 Iraqis wounded and 7,098 killed.
Mohammed Hafez' study, "Suicide Bombers in Iraq," states there have been 1,800 suicide attacks worldwide since the phenomenon began in the early 1980s. Of those, more than half have taken place in Iraq.
Records seized by the U.S. military shows that 40 percent of bombers come from North African countries such as Libya and Algeria, and 41 percent from Saudi Arabia.
Now They Tell You
I suppose this is better late then never but I think they lost their credibility with their delay.
Leaders of the 57-nation Organization of the Islamic Conference represents 1.5 billion Muslims across the Middle East, Africa, and Asia, they made their "Dakar Declaration" on Friday.
The Declaration states: "We continue to strongly condemn all forms of extremism and dogmatism which are incompatible with Islam, a religion of moderation and peaceful coexistence."
Friday, March 14, 2008
Female Warrior
Secrets of High School

This book is chock full of things I didn't know, aspects of the high school game that I should know, and tons of worthwhile and handy references.
Thursday, March 13, 2008
Bush Halves Clinton's Military Deaths
Review: Technitium MAC Address Changer v4.8

I haven't commented in a while about the free Top Ten Network tools but Technitium MAC Address Changer v4.8 may be handy to protect your home wireless network against intruders. You will need to block anyone from connecting to your network except those who have network cards with specific MAC addresses. Sounds simple enough because you can set your router to block out intruders. The question is: how do you spoof a MAC address?
You can check it with this tool. You spoof a MAC address by providing one of your existing network cards a new address. This can be done with this software that lets you change your MAC address with a few simple clicks. You run the program, highlight the network card that you want to give a spoofed MAC address, click Random MAC Address, and then click the Change Now! button. Its pretty simple. It is then easy to restore your original MAC address, once you highlight it, and click "Original MAC."
Supplemental information is included about the details concerning your network cards, including the manufacturer name, MAC address, IP, Gateway, and DNS information associated with each of your network cards. It can also renew an IP address for a card, which can help fix broken network connections.
Wednesday, March 12, 2008
`For Use Against Coalition Forces'
 Graphic source: The Long War Journal.
Graphic source: The Long War Journal.
Recently, the 2nd Battalion, 4th Brigade, 2nd Iraqi Army Division stopped a car in the Al Bakir neighborhood in Mosul, Iraq. After searching the car, the Iraqi Army found six improvised explosive devices (IEDs or roadside bombs). A typical IED contains the bomb, a cell phone detonator, and rocks or pieces of iron enclosed to injure or kill as many people as possible. The bomb is triggered by a cell phone call. The bombs are hidden with scents intended to foil bomb-sniffing dogs, in this instance, the bomb smelled like cinnamon. The detonator is labeled, "For use against Coalition forces." The driver has been detained and the Iraqi Army is now looking for the bomb factory.
Tuesday, March 11, 2008
Engineers As Jihadists

Researchers have recently raised eyebrows both within academe and in professional circles with their study noting the high incidence of engineers in jihad. One of the most well-known of course is key 9/11 plotter Ayman al-Zawahiri. The study builds on more than just one infamous example of course. In a work entitled, "Engineers of Jihad1," researchers Diego Gambetta, Nuffield College and Steffen Hertog, University of Durham, quote not only al-Zawahiri, “You have trivialized our movement by your
mundane analysis. May God have mercy on you,” but their abstract details the research. In the words of their abstract:
We find that graduates from subjects such as science, engineering,
and medicine are strongly overrepresented among Islamist movements in the
Muslim world, though not among the extremist Islamic groups which have
emerged in Western countries more recently. We also find that engineers alone
are strongly over-represented among graduates in violent groups in both
realms. This is all the more puzzling for engineers are virtually absent from
left-wing violent extremists and only present rather than over-represented
among right-wing extremists. We consider four hypotheses that could explain
this pattern. Is the engineers’ prominence among violent Islamists an accident
of history amplified through network links, or do their technical skills make
them attractive recruits? Do engineers have a ‘mindset’ that makes them a
particularly good match for Islamism, or is their vigorous radicalization
explained by the social conditions they endured in Islamic countries? We
argue that the interaction between the last two causes is the most plausible
explanation of our findings, casting a new light on the sources of Islamic
extremism and grounding macro theories of radicalization in a micro-level
perspective.
At the very least, and despite the hubbub, I wanted to quote them accurately and discover what their research suggested.
Monday, March 10, 2008
Poisoning Palestinian Children
TV channel Al-aqsa has been broadcasting an "educational" programme for 7-13 year-olds called "Tomorrow's Pioneers." The show is replete with Hamas ideology and although the characters appear to be warm and fuzzy, they are anything but. The message is stridently anti-Zionist and anti-Western, lauding Muslims and conversion to Islam while encouraging holy war and martyrs. The show degenerates to a Mickey Mouse-like figure who fights a holy war.
Getty Vocabularies for All
The tool the team built, known as the Vocabulary Coordination System (VCS), offered a single production system that allows Getty staff to collect, analyze, edit, merge and distribute terminology generated by Getty departments and contributors at other institutions.
The Getty's technical staff supports the VCS, the Getty Vocabularies on the Web, Web-based forms for the automated contribution of single records, and programs to automatically load batches of contributed data in XML format. The team also supports programs to produce yearly exports in XML, relational tables, and the Marc (Machine-readable Cataloging) format for institutions and commercial entities that license data sets.
The vocabularies average more than 900,000 searches per quarter. The vocabularies are available to the accessible to the public for free at the Getty museum.
Dutch Go Dutch
Middelkoop stated: "A greater commitment of the United Nations and other international organisations and NGOs (non-governmental organisations) is necessary to ensure that progress does not evaporate."
He continued: "Projects such as schools, health clinics, roads and power plants will not only help the economy, but also help the government to assert its authority throughout Afghanistan."
Finally, a bit of a reaction from the Coalition's European allies, and from minuscule Holland no less.
Australian and Dutch troops have been working together for 18 months in a NATO-led mission in the southern Afghan province of Uruzgan, a former Taliban stronghold.
I wish them well and it would be too much to ask that France and Germany chime in behind them but we can always hope.
Sunday, March 9, 2008
Note on Ferguson, The War of the World

In his fussy, The War of the World, Niall Ferguson presents a moral view of the twentieth century reviewing mostly secondary sources to declaim the savagery of the 20th century. Ferguson shows primarily how not only financial difficulties as well as economic progress, in short, economic volatility of any sort, along with decaying empires, psychopathic dictators, and social violence resulted in the wars, and the genocides of what he calls "History's Age of Hatred."
The book was widely acclaimed, Ferguson was interviewed and on podcasts, The New York Times Book Review named War of the World one the 100 Notable Books of the Year and acclaimed by many in 2006.
I am uncomfortable with his moralizing historical analysis which evaluates as much as it relates historical events. He seems to write a fuddy-duddy analysis of repellent dictators and economic troubles. One part of the subtitle, the Descent of the West, seems cloying or perhaps he means the phrase in an ironic nod to Darwin. I'm not sure.
Saturday, March 8, 2008
Woman Stoned to Death
Yazidis [also Yezidi, Azidi, Zedi, or Izdi] are a syncretistic religious group (or a set of several groups), with ancient origins and comprising Gnostic core belief structure with other elements of Zoroastrianism, Judaism, Christianity, Manicheism, and Islam. Yazidi do not intermarry with outsiders or accept converts. Many Yazidi now consider themselves to be Kurds, while others define themselves as both religiously and ethnically distinct from Muslim Kurds. Most of the 700,000 Yazidi reside in the North of the country. The group remains secretive even today and its teachings are obscure and may not even be fully known even to its own adherents.
Free Stanford Education
Friday, March 7, 2008
Thursday, March 6, 2008
Do You Recognize the Biker?

Police officers, one of them in a hazardous-materials suit, examined the military recruiting station in Times Square after an explosion damaged the front of the building early Thursday morning. Graphic source: Chip East/Reuters.
This may well be a dry run for a subsequent attack but video reveals a man riding on a bike who set off a small bomb at a recruiting office. The accounts are frustratingly vague on how similar the attack is to previous attacks on U.S. embassies. The bomb is also similar to attacks on recruiting centers elsewhere. On 3 May 2006 for example insurgents embarked on deadly attacks in Baghdad killing 16 people at a police recruitment center in Falluja, an American civilian contractor near Nasiriya and a police officer in Baquba; on 31 May 2007 a suicide bomber killed up to 25 people at a police recruiting center in Fallujah, though the estimated number of number of dead and injured have varied.
Wednesday, March 5, 2008
Al Qaeda Operatives Eliminated in the North
US and Iraqi security forces have killed or captured 26 senior leaders of al Qaeda in Iraq's terror network over the past several weeks. Eight of those killed were emirs, or leaders responsible for "a geographic or functional area," five were cell leaders, and 13 were facilitators "involved in supporting the network of foreign terrorists, organizing the movement and security of senior leaders of the terrorist cells, or the making and use of improvised explosives and suicide vests." Those identified highlights how al Qaeda's operations have shifted from Anbar and Baghdad provinces to the northern provinces of Diyala, Salahadin, and Ninewa. Of those al Qaeda leaders identified, five operated in Mosul, two in Tikrit, one in Sharqat, and one in Baqubah, all in the north. Only two of those identified as killed or captured came from Baghdad.
Point of Contrasting Candidates, Historically
For example, John F. Kennedy was interviewed on 3 January 1960 for the "Meet The Press" show once he announced he was running for President on the Democratic ticket. The interviewers are serious, sober, and ask numerous substantive questions. Kennedy is articulate, has a grasp of history, bases his thinking on sound reasons, he discusses and supports a foundation of thought on constitutional issues, and finally, he does not mince words on even the tough questions posed to him. The questions are directed at the candidate and they get out of the way. The overwhelming numbers of words come from Kennedy.
On the other hand, in a recent disagreement Obama and McCain spout off sound bites vapidly. Yet, the commentators, who dominate the issue, blather on blissfully about how the candidates have finally reached a point of policy and they seem thrilled that the disagreement is dealing with one issue, at least, seriously. Its just pathetic. They are gleefully mugging for the camera and note how exciting and interesting the debate is. They spew out an abundance of words, and no one seems to note that both Obama and McCain seem ignorant of the issue they are discussing. The commentators only seek to heighten the conflict.
Isn't it just by coincidence that the Meet the Press clip are all male interviewers, although it should be noted that the show included females as well, and the contemporary clip is all women?
And now a word from our sponsor.
In short, this is the focus, not any sort of issue or choice that a voter could consider. Its teletainment.
Tuesday, March 4, 2008
Saleh the Intended Victim of the Airstrike

The U.S. airstrike was in fact targetting Al Qaeda leader Saleh in the southern Somalia action. Saleh Ali Saleh Nabhan, a senior operative for al Qaeda's network in eastern Africa, was "found, targeted, and killed" along with an unspecified number of al Qaeda operatives in the town of Dhobley along the southern border with Kenya.
Nonetheless, although news reports have run the story, the U.S. military has not confirmed Saleh's death with DNA and other forensic evidence to confirm the identity of those killed in the attack.
Nabhan is also wanted for involvement in the 1998 suicide attacks against US embassies in Kenya and Tanzania. The attack in Nairobi, Kenya resulted in 212 killed and more than 4,000 wounded. The attack in Dar es Salaam, Tanzania resulted 11 killed and 85 wounded. Fazul Abdullah Mohammed, al Qaeda's operations chief in East Africa, and Abu Taha al Sudani, the leader of al Qaeda's network in East Africa were also behind the attacks.
Monday, March 3, 2008
Pakistani Censorship Technically Explained
The nefarious Pakistani deed took about two hours to correct.
BGP injections won't be fixed nor will they likely be. At times it is by accident, other times spammers or hijackers are sabotaging an address. More ominously, governments keep attempting to censor Web sites, and in the climate we are in, that kind of sabotage is likely to happen more and more.
The basic issue is that for the big network providers, relations between them still runs on trust. And as long as one of them sends out routing information to the others, we presume it to be true.
IronKey Secure the Best Stick

Computerworld surveyed 7 secure USB drives and concluded that based on features, price, security, and similar concerns, the IronKey Secure was the best of the lot. The item tested, a 4GB version, also available in 1GB and 2GB sizes, is listed at $149.99 with 128-bit AES encryption.
U.S. Airstrike in Somalia May Target Fazul
With news that a U.S. airstrike hit an al Qaeda safe house in Somalia the speculation is that the launch targeted Fazul Abdullah Mohammed, among others.
I am pleased to see that the U.S. did not check with Europe for permission before launching the strike. At least I do not know that we asked for permission. This is another individual that would not be a loss for humanity to lose.
The airstrike targeted an al Qaeda safe house in the town of Dobley in southern Somalia, just four miles from the Kenyan border.
The target of the strike has not been identified, but it may be Fazul, and the military believes the strike was successful. At least eight were reported killed and six more are reported to be trapped inside the rubble of the safe house.
This is the fourth known US-led airstrike against al Qaeda operatives in Somalia since the Ethiopian operation to drive the Islamic Courts from power was launched in late December 2006.
The US targeted Fazul Abdullah Mohammad, Saleh Ali Saleh Nabhan, and Abu Tala al Sudani during the early 2007 strikes. Fazul was again targeted in June 2007. They are believed to be sheltering in Somalia, and one or more of them may have been the target of today's strike.
Fazul is al Qaeda's operations chief responsible for planning the 1998 bombings of the US embassies in Kenya and Tanzania, as well as the 2002 car bombing attack in Kenya and missile attack on an Israeli airliner.
He needs to go.
The Hunters Are Now the Hunted
The word out on the Marines is that big game hunters are now providing training for Marines sent to Iraq.
Combat Hunter is the name of the program begun at Camp Pendleton which is now being rolled out nationwide. The program is designed to help Marines more keenly become aware of their senses and instincts while stalking and killing insurgents. The Marines are trained to be better observers while accumulating meticulous knowledge of their foes' habits.
This is a primal skill that with the enormous growth of technology in warfighting we may have lost.
On the one hand, the Marines are simply being re-trained to recognize our animal nature. We are animals, even if we are not nothing but animals. And two, they are trained killers anyway so they are no more likely to be a problem adjusting to normal live upon their return. These are two concerns that have been expressed but I believe them to be misplaced.
Although I may share concerns about an erosion of liberty, which I do, I don't see how developing a more lethal military to eliminate our enemies, is a problem.
Furthermore, viewing an enemy, as an animal as we are ourselves, does not lessen the humanity of any Marine. In response to this story, "Anonymous Hollywoood Blacklist Dodger" stated: "Finally an admission from an official goverment agency (the Marines) that we are in fact, bipedal, semi-domesticated, mostly hairless primates." Now, that's funny.
Sunday, March 2, 2008
Friedman Tells Insurgents to "Suck On This"
U.S. Combat Deaths Decrease
 Graphic source: Photo: Danfung Dennis/WPN.
Graphic source: Photo: Danfung Dennis/WPN.
Any casualties are regrettable but what can be stated positively is that U.S. casualties dropped last month.
The official U.S. troop death count in Iraq stands at 29, the third-lowest monthly casualty toll for the U.S. military since the American-led invasion in 2003. The count includes 3 non-combat deaths.
40 were killed in January, a year ago the count was 81. There has been a dramatic decrease in American troop deaths.
Although various criteria measuring violence confirms that there has been a downturn, Iraqi casualties increased which no doubt reflects the greater role that Iraqis are playing in reconstruction.
The three key factors which are widely credited with reducing violence in Iraq over the past six months are: an increase in U.S. troop levels; a cease-fire by radical cleric Muqtada al-Sadr's Mahdi Army militia; and the decision by tens of thousands of Sunni fighters to accept U.S. funding and turn against al-Qaida in Iraq.
Saturday, March 1, 2008
U.S. Rolls in Mosul
Abu Yasir al Saudi was al Qaeda in Iraq’s emir, or leader, of southeastern Mosul. Hamdan was a close associate of Yasir who helped foreign terrorists enter Mosul and led a regional anti-aircraft ring.
142 al Qaeda leaders and operatives have been killed or captured in Mosul since January in this last urban outpost of AQ.
In what is surely a harbinger of disaster for Saudi Arabia, and more importantly for the U.S. unless we cut our ties with the oppressive regime, Saudi nationals make up the largest element of the foreign al Qaeda fighters. Based on documentation found last October, 41% of foreign fighters were from Saudi Arabia. Libyan nationals accounted for the second largest group entering Iraq with about 19% of the total, followed by Syrians and Yemenis each at 8%, Algerians with 7% and Moroccans at 6%.
Total Pageviews
Popular Posts
-
The original article, which has generated an incredible amount of hits, has mysteriously disappeared: 24 November 2014. http://www.wnd.com...
-
Assessment
-
SherAli Tareen, Assistant Professor of Religious Studies at Franklin and Marshall College, was awarded an American Academy of Religion’s 201...
-
This inaugural episode in series 1 (Paul and his communities) uses incidental autobiographical references in Paul’s letters as an avenue int...
-
Londoner
-
Rockefeller, Prager University Rockefeller
-
Why is Modern Art so Bad? 5:49 For two millennia, great artists set the standard for beauty. Now those standards are gone. Modern ar...
FEEDJIT Live Traffic Feed/Site Meter
FEEDJIT Live Traffic Map
Search This Blog
Reading since summer 2006 (some of the classics are re-reads): including magazine subscriptions
- Abbot, Edwin A., Flatland;
- Accelerate: Technology Driving Business Performance;
- ACM Queue: Architecting Tomorrow's Computing;
- Adkins, Lesley and Roy A. Adkins, Handbook to Life in Ancient Rome;
- Ali, Ayaan Hirsi, Nomad: From Islam to America: A Personal Journey Through the Clash of Civilizations;
- Ali, Tariq, The Clash of Fundamentalisms: Crusades, Jihads, and Modernity;
- Allawi, Ali A., The Crisis of Islamic Civilization;
- Alperovitz, Gar, The Decision To Use the Atomic Bomb;
- American School & University: Shaping Facilities & Business Decisions;
- Angelich, Jane, What's a Mother (in-Law) to Do?: 5 Essential Steps to Building a Loving Relationship with Your Son's New Wife;
- Arad, Yitzchak, In the Shadow of the Red Banner: Soviet Jews in the War Against Nazi Germany;
- Aristotle, Athenian Constitution. Eudemian Ethics. Virtues and Vices. (Loeb Classical Library No. 285);
- Aristotle, Metaphysics: Books X-XIV, Oeconomica, Magna Moralia (The Loeb classical library);
- Armstrong, Karen, A History of God;
- Arrian: Anabasis of Alexander, Books I-IV (Loeb Classical Library No. 236);
- Atkinson, Rick, The Guns at Last Light: The War in Western Europe, 1944-1945 (Liberation Trilogy);
- Auletta, Ken, Googled: The End of the World As We Know It;
- Austen, Jane, Pride and Prejudice;
- Bacevich, Andrew, The Limits of Power: The End of American Exceptionalism;
- Baker, James A. III, and Lee H. Hamilton, The Iraq Study Group Report: The Way Forward - A New Approach;
- Barber, Benjamin R., Jihad vs. McWorld: Terrorism's Challenge to Democracy;
- Barnett, Thomas P.M., Blueprint for Action: A Future Worth Creating;
- Barnett, Thomas P.M., The Pentagon's New Map: War and Peace in the Twenty-First Century;
- Barron, Robert, Catholicism: A Journey to the Heart of the Faith;
- Baseline: Where Leadership Meets Technology;
- Baur, Michael, Bauer, Stephen, eds., The Beatles and Philosophy;
- Beard, Charles Austin, An Economic Interpretation of the Constitution of the United States (Sony Reader);
- Benjamin, Daniel & Steven Simon, The Age of Sacred Terror: Radical Islam's War Against America;
- Bergen, Peter, The Osama bin Laden I Know: An Oral History of al Qaeda's Leader;
- Berman, Paul, Terror and Liberalism;
- Berman, Paul, The Flight of the Intellectuals: The Controversy Over Islamism and the Press;
- Better Software: The Print Companion to StickyMinds.com;
- Bleyer, Kevin, Me the People: One Man's Selfless Quest to Rewrite the Constitution of the United States of America;
- Boardman, Griffin, and Murray, The Oxford Illustrated History of the Roman World;
- Bracken, Paul, The Second Nuclear Age: Strategy, Danger, and the New Power Politics;
- Bradley, James, with Ron Powers, Flags of Our Fathers;
- Bronte, Charlotte, Jane Eyre;
- Bronte, Emily, Wuthering Heights;
- Brown, Ashley, War in Peace Volume 10 1974-1984: The Marshall Cavendish Encyclopedia of Postwar Conflict;
- Brown, Ashley, War in Peace Volume 8 The Marshall Cavendish Illustrated Encyclopedia of Postwar Conflict;
- Brown, Nathan J., When Victory Is Not an Option: Islamist Movements in Arab Politics;
- Bryce, Robert, Gusher of Lies: The Dangerous Delusions of "Energy Independence";
- Bush, George W., Decision Points;
- Bzdek, Vincent, The Kennedy Legacy: Jack, Bobby and Ted and a Family Dream Fulfilled;
- Cahill, Thomas, Sailing the Wine-Dark Sea: Why the Greeks Matter;
- Campus Facility Maintenance: Promoting a Healthy & Productive Learning Environment;
- Campus Technology: Empowering the World of Higher Education;
- Certification: Tools and Techniques for the IT Professional;
- Channel Advisor: Business Insights for Solution Providers;
- Chariton, Callirhoe (Loeb Classical Library);
- Chief Learning Officer: Solutions for Enterprise Productivity;
- Christ, Karl, The Romans: An Introduction to Their History and Civilization;
- Cicero, De Senectute;
- Cicero, The Republic, The Laws;
- Cicero, The Verrine Orations I: Against Caecilius. Against Verres, Part I; Part II, Book 1 (Loeb Classical Library);
- Cicero, The Verrine Orations I: Against Caecilius. Against Verres, Part I; Part II, Book 2 (Loeb Classical Library);
- CIO Decisions: Aligning I.T. and Business in the MidMarket Enterprise;
- CIO Insight: Best Practices for IT Business Leaders;
- CIO: Business Technology Leadership;
- Clay, Lucius Du Bignon, Decision in Germany;
- Cohen, William S., Dragon Fire;
- Colacello, Bob, Ronnie and Nancy: Their Path to the White House, 1911 to 1980;
- Coll, Steve, The Bin Ladens: An Arabian Family in the American Century;
- Collins, Francis S., The Language of God: A Scientist Presents Evidence for Belief ;
- Colorni, Angelo, Israel for Beginners: A Field Guide for Encountering the Israelis in Their Natural Habitat;
- Compliance & Technology;
- Computerworld: The Voice of IT Management;
- Connolly, Peter & Hazel Dodge, The Ancient City: Life in Classical Athens & Rome;
- Conti, Greg, Googling Security: How Much Does Google Know About You?;
- Converge: Strategy and Leadership for Technology in Education;
- Cowan, Ross, Roman Legionary 58 BC - AD 69;
- Cowell, F. R., Life in Ancient Rome;
- Creel, Richard, Religion and Doubt: Toward a Faith of Your Own;
- Cross, Robin, General Editor, The Encyclopedia of Warfare: The Changing Nature of Warfare from Prehistory to Modern-day Armed Conflicts;
- CSO: The Resource for Security Executives:
- Cummins, Joseph, History's Greatest Wars: The Epic Conflicts that Shaped the Modern World;
- D'Amato, Raffaele, Imperial Roman Naval Forces 31 BC-AD 500;
- Dallek, Robert, An Unfinished Life: John F. Kennedy 1917-1963;
- Daly, Dennis, Sophocles' Ajax;
- Dando-Collins, Stephen, Caesar's Legion: The Epic Saga of Julius Caesar's Elite Tenth Legion and the Armies of Rome;
- Darwish, Nonie, Now They Call Me Infidel: Why I Renounced Jihad for America, Israel, and the War on Terror;
- Davis Hanson, Victor, Makers of Ancient Strategy: From the Persian Wars to the Fall of Rome;
- Dawkins, Richard, The Blind Watchmaker;
- Dawkins, Richard, The God Delusion;
- Dawkins, Richard, The Selfish Gene;
- de Blij, Harm, Why Geography Matters: Three Challenges Facing America, Climate Change, The Rise of China, and Global Terrorism;
- Defense Systems: Information Technology and Net-Centric Warfare;
- Defense Systems: Strategic Intelligence for Info Centric Operations;
- Defense Tech Briefs: Engineering Solutions for Military and Aerospace;
- Dennett, Daniel C., Breaking the Spell: Religion as a Natural Phenomenon;
- Dennett, Daniel C., Consciousness Explained;
- Dennett, Daniel C., Darwin's Dangerous Idea;
- Devries, Kelly, et. al., Battles of the Ancient World 1285 BC - AD 451 : From Kadesh to Catalaunian Field;
- Dickens, Charles, Great Expectations;
- Digital Communities: Building Twenty-First Century Communities;
- Doctorow, E.L., Homer & Langley;
- Dodds, E. R., The Greeks and the Irrational;
- Dostoevsky, Fyodor, The House of the Dead (Google Books, Sony e-Reader);
- Dostoevsky, Fyodor, The Idiot;
- Douglass, Elisha P., Rebels and Democrats: The Struggle for Equal Political Rights and Majority Role During the American Revolution;
- Doyle, Sir Arthur Conan, The Hound of the Baskervilles & The Valley of Fear;
- Dr. Dobb's Journal: The World of Software Development;
- Drug Discovery News: Discovery/Development/Diagnostics/Delivery;
- DT: Defense Technology International;
- Dunbar, Richard, Alcatraz;
- Education Channel Partner: News, Trends, and Analysis for K-20 Sales Professionals;
- Edwards, Aton, Preparedness Now!;
- EGM: Electronic Gaming Monthly, the No. 1 Videogame Magazine;
- Ehrman, Bart D., Lost Christianities: The Battles for Scriptures and the Faiths We Never Knew;
- Ehrman, Bart D., Misquoting Jesus: The Story Behind Who Changed the Bible and Why;
- Electronic Engineering Times: The Industry Newsweekly for the Creators of Technology;
- Ellis, Joseph J., American Sphinx: The Character of Thomas Jefferson;
- Ellis, Joseph J., His Excellency: George Washington;
- Emergency Management: Strategy & Leadership in Critical Times;
- Emerson, Steven, American Jihad: The Terrorists Living Among Us;
- Erlewine, Robert, Monotheism and Tolerance: Recovering a Religion of Reason (Indiana Series in the Philosophy of Religion);
- ESD: Embedded Systems Design;
- Everitt, Anthony, Augustus: The Life of Rome's First Emperor;
- Everitt, Anthony, Cicero: The Life and Times of Rome's Greatest Politician;
- eWeek: The Enterprise Newsweekly;
- Federal Computer Week: Powering the Business of Government;
- Ferguson, Niall, Civilization: The West and the Rest;
- Ferguson, Niall, Empire: The Rise and Demise of the British World Order and the Lessons for Global Power;
- Ferguson, Niall, The Cash Nexus: Money and Power in the Modern World, 1700-2000;
- Ferguson, Niall, The War of the World: Twentieth-Century Conflict and the Decline of the West;
- Feuerbach, Ludwig, The Essence of Christianity (Sony eReader);
- Fields, Nic, The Roman Army of the Principate 27 BC-AD 117;
- Fields, Nic, The Roman Army of the Punic Wars 264-146 BC;
- Fields, Nic, The Roman Army: the Civil Wars 88-31 BC;
- Finkel, Caroline, Osman's Dream: The History of the Ottoman Empire;
- Fisk, Robert, The Great War For Civilization: The Conquest of the Middle East;
- Forstchen, William R., One Second After;
- Fox, Robin Lane, The Classical World: An Epic History from Homer to Hadrian;
- Frazer, James George, The Golden Bough (Volume 3): A Study in Magic and Religion (Sony eReader);
- Freeh, Louis J., My FBI: Bringing Down the Mafia, Investigating Bill Clinton, and Fighting the War on Terror;
- Freeman, Charles, The Greek Achievement: The Foundations of the Western World;
- Friedman, Thomas L. The World Is Flat: A Brief History of the Twenty-First Century Further Updated and Expanded/Release 3.0;
- Friedman, Thomas L., The Lexus and the Olive Tree: Understanding Globalization;
- Frontinus: Stratagems. Aqueducts of Rome. (Loeb Classical Library No. 174);
- Fuller Focus: Fuller Theological Seminary;
- Fuller, Graham E., A World Without Islam;
- Gaubatz, P. David and Paul Sperry, Muslim Mafia: Inside the Secret Underworld That's Conspiring to Islamize America;
- Ghattas, Kim, The Secretary: A Journey with Hillary Clinton from Beirut to the Heart of American Power;
- Gibson, William, Neuromancer;
- Gilmour, Michael J., Gods and Guitars: Seeking the Sacred in Post-1960s Popular Music;
- Global Services: Strategies for Sourcing People, Processes, and Technologies;
- Glucklich, Ariel, Dying for Heaven: Holy Pleasure and Suicide Bombers-Why the Best Qualities of Religion Are Also It's Most Dangerous;
- Goldberg, Jonah, Liberal Fascism: The Secret History of the American Left, From Mussolini to the Politics of Meaning;
- Goldin, Shmuel, Unlocking the Torah Text Vayikra (Leviticus);
- Goldsworthy, Adrian, Caesar: Life of a Colossus;
- Goldsworthy, Adrian, How Rome Fell: Death of a Superpower;
- Goodman, Lenn E., Creation and Evolution;
- Goodwin, Doris Kearns, Team of Rivals: The Political Genius of Abraham Lincoln;
- Gopp, Amy, et.al., Split Ticket: Independent Faith in a Time of Partisan Politics (WTF: Where's the Faith?);
- Gordon, Michael R., and Bernard E. Trainor, Cobra II: The Inside Story of the Invasion and Occupation of Iraq;
- Government Health IT: The Magazine of Public/private Health Care Convergence;
- Government Technology's Emergency Management: Strategy & Leadership in Critical Times;
- Government Technology: Solutions for State and Local Government in the Information Age;
- Grant , Michael, The Climax of Rome: The Final Achievements of the Ancient World, AD 161 - 337;
- Grant, Michael, The Classical Greeks;
- Grumberg, Orna, and Helmut Veith, 25 Years of Model Checking: History, Achievements, Perspectives;
- Halberstam, David, War in a Time of Peace: Bush, Clinton, and the Generals;
- Hammer, Reuven, Entering Torah Prefaces to the Weekly Torah Portion;
- Hanson, Victor Davis, An Autumn of War: What America Learned from September 11 and the War on Terrorism;
- Hanson, Victor Davis, Between War and Peace: Lessons from Afghanistan to Iraq;
- Hanson, Victor Davis, Carnage and Culture: Landmark Battles in the Rise of Western Power;
- Hanson, Victor Davis, How The Obama Administration Threatens Our National Security (Encounter Broadsides);
- Hanson, Victor Davis, Makers of Ancient Strategy: From the Persian Wars to the Fall of Rome;
- Hanson, Victor Davis, Ripples of Battle: How Wars of the Past Still Determine How We Fight, How We Live, and How We Think;
- Hanson, Victor Davis, The End of Sparta: A Novel;
- Hanson, Victor Davis, The Soul of Battle: From Ancient Times to the Present Day, How Three Great Liberators Vanquished Tyranny;
- Hanson, Victor Davis, Wars of the Ancient Greeks;
- Harnack, Adolf Von, History of Dogma, Volume 3 (Sony Reader);
- Harris, Alex, Reputation At Risk: Reputation Report;
- Harris, Sam, Letter to a Christian Nation;
- Harris, Sam, The End of Faith: Religion, Terror, and the Future of Reason;
- Hayek, F. A., The Road to Serfdom;
- Heilbroner, Robert L., and Lester Thurow, Economics Explained: Everything You Need to Know About How the Economy Works and Where It's Going;
- Hempel, Sandra, The Strange Case of The Broad Street Pump: John Snow and the Mystery of Cholera;
- Hinnells, John R., A Handbook of Ancient Religions;
- Hitchens, Christopher, God Is Not Great: How Religion Poisons Everything;
- Hogg, Ian V., The Encyclopedia of Weaponry: The Development of Weaponry from Prehistory to 21st Century Warfare;
- Hugo, Victor, The Hunchback of Notre Dame;
- Humphrey, Caroline & Vitebsky, Piers, Sacred Architecture;
- Huntington, Samuel P., The Clash of Civilizations and the Remaking of World Order;
- Info World: Information Technology News, Computer Networking & Security;
- Information Week: Business Innovation Powered by Technology:
- Infostor: The Leading Source for Enterprise Storage Professionals;
- Infrastructure Insite: Bringing IT Together;
- Insurance Technology: Business Innovation Powered by Technology;
- Integrated Solutions: For Enterprise Content Management;
- Intel Premier IT: Sharing Best Practices with the Information Technology Community;
- Irwin, Robert, Dangerous Knowledge: Orientalism and Its Discontents;
- Jeffrey, Grant R., The Global-Warming Deception: How a Secret Elite Plans to Bankrupt America and Steal Your Freedom;
- Jewkes, Yvonne, and Majid Yar, Handbook of Internet Crime;
- Johnson, Chalmers, Blowback: The Costs and Consequences of American Empire;
- Journal, The: Transforming Education Through Technology;
- Judd, Denis, The Lion and the Tiger: The Rise and Fall of the British Raj, 1600-1947;
- Kagan, Donald, The Peloponnesian War;
- Kansas, Dave, The Wall Street Journal Guide to the End of Wall Street as We Know It: What You Need to Know About the Greatest Financial Crisis of Our Time--and How to Survive It;
- Karsh, Efraim, Islamic Imperialism: A History;
- Kasser, Rodolphe, The Gospel of Judas;
- Katz, Solomon, The Decline of Rome and the Rise of Medieval Europe: (The Development of Western Civilization);
- Keegan, John, Intelligence in War: The Value--and Limitations--of What the Military Can Learn About the Enemy;
- Kenis, Leo, et. al., The Transformation of the Christian Churches in Western Europe 1945-2000 (Kadoc Studies on Religion, Culture and Society 6);
- Kepel, Gilles, Jihad: The Trail of Political Islam;
- Kiplinger's: Personal Finance;
- Klein, Naomi, The Shock Doctrine: The Rise of Disaster Capitalism;
- KM World: Content, Document, and Knowledge Management;
- Koestler, Arthur, Darkness at Noon: A Novel;
- Kostova, Elizabeth, The Historian;
- Kuttner, Robert, The Squandering of America: How the Failure of Our Politics Undermines Our Prosperity;
- Lake, Kirsopp, The Text of the New Testament, Sony Reader;
- Laur, Timothy M., Encyclopedia of Modern US Military Weapons ;
- Leffler, Melvyn P., and Jeffrey W. Legro, To Lead the World: American Strategy After the Bush Doctrine;
- Lendon, J. E., Soldiers and Ghosts: A History of Battle in Classical Antiquity;
- Lenin, V. I., Imperialism the Highest Stage of Capitalism;
- Lennon, John J., There is Absolutely No Reason to Pay Too Much for College!;
- Lewis, Bernard, The Crisis of Islam: Holy War and Unholy Terror;
- Lewis, Bernard, What Went Wrong?: The Clash Between Islam and Modernity in the Middle East;
- Lifton, Robert J., Greg Mitchell, Hiroshima in America;
- Limberis, Vasiliki M., Architects of Piety: The Cappadocian Fathers and the Cult of the Martyrs;
- Lipsett, B. Diane, Desiring Conversion: Hermas, Thecla, Aseneth;
- Livingston, Jessica, Founders At Work: Stories of Startups' Early Days;
- Livy, Rome and the Mediterranean: Books XXXI-XLV of the History of Rome from its Foundation (Penguin Classics);
- Louis J., Freeh, My FBI: Bringing Down the Mafia, Investigating Bill Clinton, and Fighting the War on Terror;
- Mackay, Christopher S., Ancient Rome: A Military and Political History;
- Majno, Guido, The Healing Hand: Man and Wound in the Ancient World;
- Marcus, Greil,Invisible Republic: Bob Dylan's Basement Tapes;
- Marshall-Cornwall, James, Napoleon as Military Commander;
- Maughm, W. Somerset, Of Human Bondage;
- McCluskey, Neal P., Feds in the Classroom: How Big Government Corrupts, Cripples, and Compromises American Education;
- McCullough, David, 1776;
- McCullough, David, John Adams;
- McCullough, David, Mornings on Horseback: The Story of an Extraordinary Family, a Vanished Way of Life and the Unique Child Who Became Theodore Roosevelt;
- McLynn, Frank, Marcus Aurelius: A Life;
- McManus, John, Deadly Brotherhood, The: The American Combat Soldier in World War II ;
- McMaster, H. R., Dereliction of Duty: Johnson, McNamara, the Joint Chiefs of Staff, and the Lies That Led to Vietnam;
- McNamara, Patrick, Science and the World's Religions Volume 1: Origins and Destinies (Brain, Behavior, and Evolution);
- McNamara, Patrick, Science and the World's Religions Volume 2: Persons and Groups (Brain, Behavior, and Evolution);
- McNamara, Patrick, Science and the World's Religions Volume 3: Religions and Controversies (Brain, Behavior, and Evolution);
- Meacham, Jon, American Lion: Andrew Jackson in the White House;
- Mearsheimer, John J., and Stephen M. Walt, The Israel Lobby and U.S. Foreign Policy;
- Meier, Christian, Caesar: A Biography;
- Menzies, Gaven, 1421: The Year China Discovered America;
- Metaxas, Eric, Bonhoeffer: Pastor, Martyr, Prophet, Spy;
- Michael, Katina and M.G. Michael, Innovative Automatic Identification and Location-Based Services: From Barcodes to Chip Implants;
- Migliore, Daniel L., Faith Seeking Understanding: An Introduction to Christian Theology;
- Military & Aerospace Electronics: The Magazine of Transformation in Electronic and Optical Technology;
- Millard, Candice, Theodore Roosevelt's Darkest Journey: The River of Doubt;
- Mommsen, Theodor, The History of the Roman Republic, Sony Reader;
- Muller, F. Max, Chips From A German Workshop: Volume III: Essays On Language And Literature;
- Murray, Janet, H., Hamlet On the Holodeck: The Future of Narrative in Cyberspace;
- Murray, Williamson, War in the Air 1914-45;
- Müller, F. Max, Chips From A German Workshop;
- Nader, Ralph, Crashing the Party: Taking on the Corporate Government in an Age of Surrender;
- Nagl, John A., Learning to Eat Soup with a Knife: Counterinsurgency Lessons from Malaya and Vietnam;
- Napoleoni, Loretta, Terrorism and the Economy: How the War on Terror is Bankrupting the World;
- Nature: The International Weekly Journal of Science;
- Negus, Christopher, Fedora 6 and Red Hat Enterprise Linux;
- Network Computing: For IT by IT:
- Network World: The Leader in Network Knowledge;
- Network-centric Security: Where Physical Security & IT Worlds Converge;
- Newman, Paul B., Travel and Trade in the Middle Ages;
- Nietzsche, Friedrich Wilhelm, The Nietzsche-Wagner Correspondence;
- Nixon, Ed, The Nixons: A Family Portrait;
- O'Brien, Johnny, Day of the Assassins: A Jack Christie Novel;
- O'Donnell, James J., Augustine: A New Biography;
- OH & S: Occupational Health & Safety
- Okakura, Kakuzo, The Book of Tea;
- Optimize: Business Strategy & Execution for CIOs;
- Ostler, Nicholas, Ad Infinitum: A Biography of Latin;
- Parry, Jay A., The Real George Washington (American Classic Series);
- Paton, W.R., The Greek Anthology, Volume V, Loeb Classical Library, No. 86;
- Pausanius, Guide to Greece 1: Central Greece;
- Perrett, Bryan, Cassell Military Classics: Iron Fist: Classic Armoured Warfare;
- Perrottet, Tony, The Naked Olympics: The True Story of the Olympic Games;
- Peters, Ralph, New Glory: Expanding America's Global Supremacy;
- Phillips, Kevin, American Dynasty: Aristocracy, Fortune, and the Politics of Deceit in the House of Bush;
- Pick, Bernhard; Paralipomena; Remains of Gospels and Sayings of Christ (Sony Reader);
- Pimlott, John, The Elite: The Special Forces of the World Volume 1;
- Pitre, Brant, Jesus and the Jewish Roots of the Eucharist: Unlocking the Secrets of the Last Supper;
- Plutarch's Lives, X: Agis and Cleomenes. Tiberius and Gaius Gracchus. Philopoemen and Flamininus (Loeb Classical Library®);
- Podhoretz, Norman, World War IV: The Long Struggle Against Islamofascism;
- Posner, Gerald, Case Closed: Lee Harvey Oswald and the Assassination of JFK;
- Potter, Wendell, Deadly Spin: An Insurance Company Insider Speaks Out on How Corporate PR Is Killing Health Care and Deceiving Americans;
- Pouesi, Daniel, Akua;
- Premier IT Magazine: Sharing Best Practices with the Information Technology Community;
- Price, Monroe E. & Daniel Dayan, eds., Owning the Olympics: Narratives of the New China;
- Profit: The Executive's Guide to Oracle Applications;
- Public CIO: Technology Leadership in the Public Sector;
- Putnam, Robert D., Bowling Alone : The Collapse and Revival of American Community;
- Quintus of Smyrna, The Fall of Troy;
- Rawles, James Wesley, Patriots: A Novel of Survival in the Coming Collapse;
- Red Herring: The Business of Technology;
- Redmond Channel Partner: Driving Success in the Microsoft Partner Community;
- Redmond Magazine: The Independent Voice of the Microsoft IT Community;
- Renan, Ernest, The life of Jesus (Sony eReader);
- Richler, Mordecai (editor), Writers on World War II: An Anthology;
- Roberts, Ian, The Energy Glut: Climate Change and the Politics of Fatness in an Overheating World;
- Rocca, Samuel, The Army of Herod the Great;
- Rodgers, Nigel, A Military History of Ancient Greece: An Authoritative Account of the Politics, Armies and Wars During the Golden Age of Ancient Greece, shown in over 200 color photographs, diagrams, maps and plans;
- Rodoreda, Merce, Death in Spring: A Novel;
- Romerstein, Herbert and Breindel, Eric,The Venona Secrets, Exposing Soviet Espionage and America's Traitors;
- Ross, Dennis, Statecraft: And How to Restore America's Standing in the World;
- Roth, Jonathan P., Roman Warfare (Cambridge Introduction to Roman Civilization);
- SC Magazine: For IT Security Professionals;
- Scahill, Jeremy, Blackwater: The Rise of the World's Most Powerful Mercenary Army [Revised and Updated];
- Schama, Simon, A History of Britain, At the Edge of the World 3500 B.C. - 1603 A.D.;
- Scheuer, Michael, Imperial Hubris: Why the West Is Losing the War On Terror;
- Scheuer, Michael, Marching Toward Hell: America and Islam After Iraq;
- Scheuer, Michael, Osama Bin Laden;
- Scheuer, Michael, Through Our Enemies Eyes: Osama Bin Laden, Radical Islam, and the Future of America;
- Scholastic Instructor
- Scholastic Parent & Child: The Joy of Family Living and Learning;
- Schopenhauer, Arthur, The World As Will And Idea (Sony eReader);
- Schug-Wille, Art of the Byzantine World;
- Schulze, Hagen, Germany: A New History;
- Schweizer, Peter, Architects of Ruin: How Big Government Liberals Wrecked the Global Economy---and How They Will Do It Again If No One Stops Them;
- Scott, Sir Walter, Ivanhoe;
- Seagren, Eric, Secure Your Network for Free: Using Nmap, Wireshark, Snort, Nessus, and MRTG;
- Security Technology & Design: The Security Executive's Resource for Systems Integration and Convergence;
- Seibel, Peter, Coders at Work;
- Sekunda N., & S. Northwood, Early Roman Armies;
- Seneca: Naturales Quaestiones, Books II (Loeb Classical Library No. 450);
- Sewall, Sarah, The U.S. Army/Marine Corps Counterinsurgency Field Manual;
- Sheppard, Ruth, Alexander the Great at War: His Army - His Battles - His Enemies;
- Shinder, Jason, ed., The Poem That Changed America: "Howl" Fifty Years Later;
- Sidebottom, Harry, Ancient Warfare: A Very Short Introduction;
- Sides, Hampton, Blood and Thunder: The Epic Story of Kit Carson and the Conquest of the American West;
- Simkins, Michael, The Roman Army from Caesar to Trajan;
- Sinchak, Steve, Hacking Windows Vista;
- Smith, RJ, The One: The Life and Music of James Brown;
- Software Development Times: The Industry Newspaper for Software Development Managers;
- Software Test Performance;
- Solomon, Norman, War Made Easy: How Presidents and Pundits Keep Spinning Us to Death;
- Song, Lolan, Innovation Together: Microsoft Research Asia Academic Research Collaboration;
- Sophocles, The Three Theban Plays, tr. Robert Fagles;
- Sound & Vision: The Consumer Electronics Authority;
- Southern, Pat, The Roman Army: A Social and Institutional History;
- Sri, Edward, A Biblical Walk Through the Mass: Understanding What We Say and Do In The Liturgy;
- Sri, Edward, Men, Women and the Mystery of Love: Practical Insights from John Paul II's Love and Responsibility;
- Stair, John Bettridge, Old Samoa; Or, Flotsam and Jetsam From the Pacific Ocean;
- Starr, Chester G., The Roman Empire, 27 B.C.-A.D. 476: A Study in Survival;
- Starr, John Bryan, Understanding China: A Guide to China's Economy, History, and Political Culture;
- Stauffer, John, Giants: The Parallel Lives of Frederick Douglass and Abraham Lincoln;
- Steyn, Mark, America Alone: The End of the World As We Know It;
- Strassler, Robert B., The Landmark Herodotus: The Histories;
- Strassler, Robert B., The Landmark Thucydides: A Comprehensive Guide to the Peloponnesian War;
- Strassler, Robert B., The Landmark Xenophon's Hellenika;
- Strategy + Business;
- Streete, Gail, Redeemed Bodies: Women Martyrs in Early Christianity;
- Sullivan, James, The Hardest Working Man: How James Brown Saved the Soul of America;
- Sumner, Graham, Roman Military Clothing (1) 100 BC-AD 200;
- Sumner, Graham, Roman Military Clothing (2) AD 200-400;
- Suskind, Ron, The One Percent Doctrine: Deep Inside America's Pursuit of Its Enemies Since 9/11:
- Swanston, Malcolm, Mapping History Battles and Campaigns;
- Swiderski, Richard M., Quicksilver: A History of the Use, Lore, and Effects of Mercury;
- Swiderski, Richard M., Quicksilver: A History of the Use, Lore, and Effects of Mercury;
- Swift, Jonathan, Gulliver's Travels;
- Syme, Ronald, The Roman Revolution;
- Talley, Colin L., A History of Multiple Sclerosis;
- Tawil, Camille, Brothers In Arms: The Story of al-Qa'ida and the Arab Jihadists;
- Tech Briefs: Engineering Solutions for Design & Manufacturing;
- Tech Net: The Microsoft Journal for IT Professionals;
- Tech Partner: Gain a Competitive Edge Through Solutions Providers;
- Technology & Learning: Ideas and Tools for Ed Tech Leaders;
- Tenet, George, At the Center of the Storm: The CIA During America's Time of Crisis;
- Thackeray, W. M., Vanity Fair;
- Thompson, Derrick & William Martin, Have Guitars ... Will Travel: A Journey Through the Beat Music Scene in Northampton 1957-66;
- Tolstoy, Leo, Anna Karenina;
- Trento, Joseph J., The Secret History of the CIA;
- Twain, Mark, The Gilded Age: a Tale of Today;
- Ungar, Craig, House of Bush House of Saud;
- Unterberger, Richie, The Unreleased Beatles Music & Film;
- VAR Business: Strategic Insight for Technology Integrators:
- Virgil, The Aeneid
- Virtualization Review: Powering the New IT Generation;
- Visual Studio: Enterprise Solutions for .Net Development;
- VON Magazine: Voice, Video & Vision;
- Wall Street Technology: Business Innovation Powered by Technology;
- Wallace, Robert, Spycraft: The Secret History of the CIA's Spytechs, from Communism to al-Qaeda;
- Wang, Wallace, Steal This Computer Book 4.0: What They Won’t Tell You About the Internet;
- Ward-Perkins, The Fall of Rome and the End of Civilization;
- Warren, Robert Penn, All the King's Men;
- Wasik, John F., Cul-de-Sac Syndrome: Turning Around the Unsustainable American Dream;
- Weber, Karl, Editor, Lincoln: A President for the Ages;
- Website Magazine: The Magazine for Website Success;
- Weiner, Tim, Enemies: A History of the FBI;
- Weiner, Tim, Legacy of Ashes: The History of the CIA;
- West, Bing, The Strongest Tribe: War, Politics, and the Endgame in Iraq;
- Wharton, Edith, The Age of Innocence;
- Wilcox, Peter, Rome's Enemies (1) Germanics and Dacians;
- Wise, Terence, Armies of the Carthaginian Wars 265 - 146 BC;
- Wissner-Gross, What Colleges Don't Tell You (And Other Parents Don't Want You To Know) 272 Secrets For Getting Your Kid Into the Top Schools;
- Wissner-Gross, What High Schools Don't Tell You;
- Wolf, Naomi, Give Me Liberty: A Handbook for American Revolutionaries;
- Wolf, Naomi, The End of America: Letter of Warning to a Young Patriot;
- Woodward, Bob, Plan of Attack;
- Woodward, Bob, The Agenda: Inside the Clinton White House;
- Wright, Lawrence, The Looming Tower: Al-Qaeda and the Road to 9/11;
- Wright-Porto, Heather, Beginning Google Blogger;
- Xenophon, The Anabasis of Cyrus;
- Yergin, Daniel, The Prize: The Epic Quest for Oil, Money, & Power;
Computing Reviews
Handy Tools, Links, etc.
Share |
CIO and Strategy & Business magazines
Nature: International Weekly Journal of Science
SD Times: Software Development News
SC Magazine for Security Professionals
Missile Defense
33 Minutes
Government Technology: Solutions for State and Local Government in the Information Age
What's Running is a great tool so that you can see what is running on your desktop.
Process Lasso lets you view your processor and its responsiveness.
Online Armor lets you view your firewall status.
Avast is a terrific scrubber of all virus miscreants.
ClamWin is an effective deterrent for the little nasty things that can crop into your machine.
Ad-Aware is a sound anti-virus tool.
For all your electronic appliance needs research products on this terrific site.
This work is licensed under a Creative Commons Attribution-Share Alike 3.0 Unported License.
Recent Comments
Blog Smith Headline Animator
Library Thing: Chicks Dig Readers
Blog Archive
-
▼
2008
(775)
-
▼
March
(54)
- Iraq Begins to Stand on its Own Two Feet
- Historians Weigh in On Iraq
- Is Iraq the New Lebanon?
- Rogue Scanner
- Basra: At the Worst, Same as It Ever Was
- Apple Easiest to Cherry Pick
- Basra Analysis
- AbiWord: Free and Lite and Easy
- Sarkozy Does Not Make a Crowd
- Obama's Taxes
- Non-U.S. Citizens Serve in the Military
- Tepid Network Solutions Bows to Islamic Pressure
- Saudi Government Trains for Prayer
- Bombing Distinction for Germany
- U.S. Top Spot for Iraqis
- "The Real Living Culture Is Western Culture"
- Obama Consistently Wrong On Iraq
- Lessig to Change Congress
- Sarkozy to Send 1,000+ Troops to Afghanistan
- Obama's Passport Breached Repeatedly
- Beckstrom the Starfish
- Audio Message Crusades Against the West
- Audacity of Obama
- The First Internet War
- How One Person Can Shut Down a Terrorist
- Guarded Optimism About Vital Indicators
- Iraqis: Blood for Oil
- Senators Lining Up to the Trough
- Who Makes a Good Bomber?
- Now They Tell You
- Female Warrior
- Secrets of High School
- Bush Halves Clinton's Military Deaths
- Review: Technitium MAC Address Changer v4.8
- `For Use Against Coalition Forces'
- Engineers As Jihadists
- Poisoning Palestinian Children
- Getty Vocabularies for All
- Dutch Go Dutch
- Note on Ferguson, The War of the World
- Woman Stoned to Death
- Free Stanford Education
- Iraqi Order of Battle Released
- Do You Recognize the Biker?
- Al Qaeda Operatives Eliminated in the North
- Point of Contrasting Candidates, Historically
- Saleh the Intended Victim of the Airstrike
- Pakistani Censorship Technically Explained
- IronKey Secure the Best Stick
- U.S. Airstrike in Somalia May Target Fazul
- The Hunters Are Now the Hunted
- Friedman Tells Insurgents to "Suck On This"
- U.S. Combat Deaths Decrease
- U.S. Rolls in Mosul
-
▼
March
(54)
National Debt Clock
"Congress: I'm Watching"
A tax on toilet paper; I kid you not. According to the sponsor, "the Water Protection and Reinvestment Act will be financed broadly by small fees on such things as . . . products disposed of in waste water." Congress wants to tax what you do in the privacy of your bathroom.
About me:
Portrait of Thinking Hero

1844-1900
Photos
Check out:
Chicks dig readers.






